A whopping 60,000+ Android apps loaded adware generating revenue for attackers
The adware ended up on apps installed using APKs offered on third-party app store websites
It is important to note that these apps were not listed in the Google Play Store and were found in third-party app store websites discovered via Google Search that use APKs (Android Packages) to allow users to sideload these malicious apps on their Android phones. When visiting these websites, users are redirected to ads or prompted to search for the app that they want. The sites are designed to install the apps via an APK which ends up infecting the user’s phone with adware.
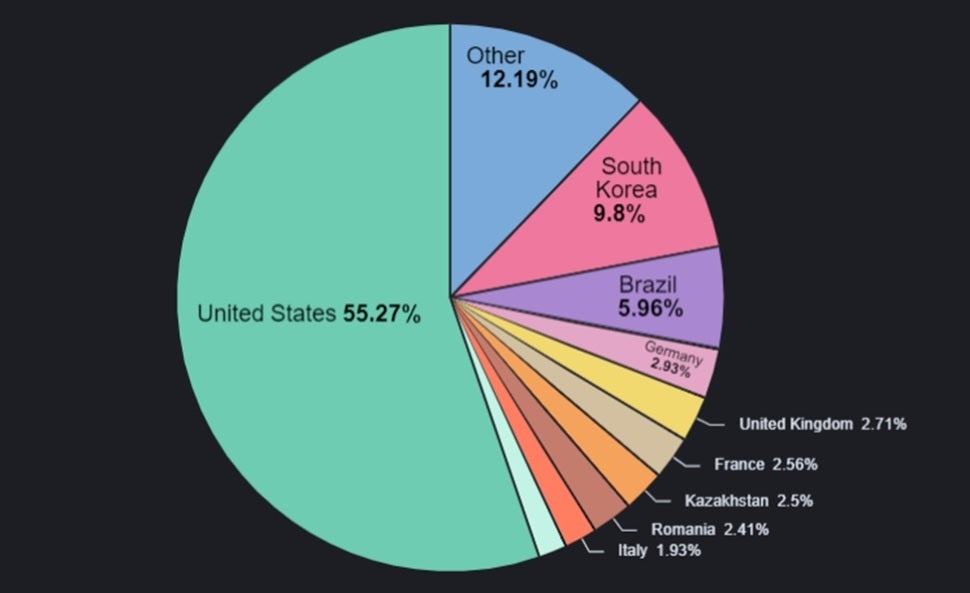
Over 55% of the malicious apps were targeted to U.S. Android users
These apps do not create an icon for the home screen which means that if it is not opened immediately using the “Open” prompt seen after installation, the app might not be opened at any time by the user. So the developers of these malware-laden apps want you to open the app immediately after it is installed. And if you do, you will see a notification that says, “Application is unavailable in your region. Tap OK to uninstall.”
While it is adware now, these apps could end up opening more malicious and dangerous websites
But the app really is not uninstalled as it sleeps for two hours; during this time the software sets itself up to launch once the phone is booted or unlocked. When the app is launched, it connects to the servers belonging to the attackers and collects URLs of ads that it will show in the mobile browser or as full-screen WebView ads. And while showing ads to ring up revenue is what these apps currently do, researchers warn that the bad actors could switch the adware URLs and have these apps open more malicious and dangerous websites.
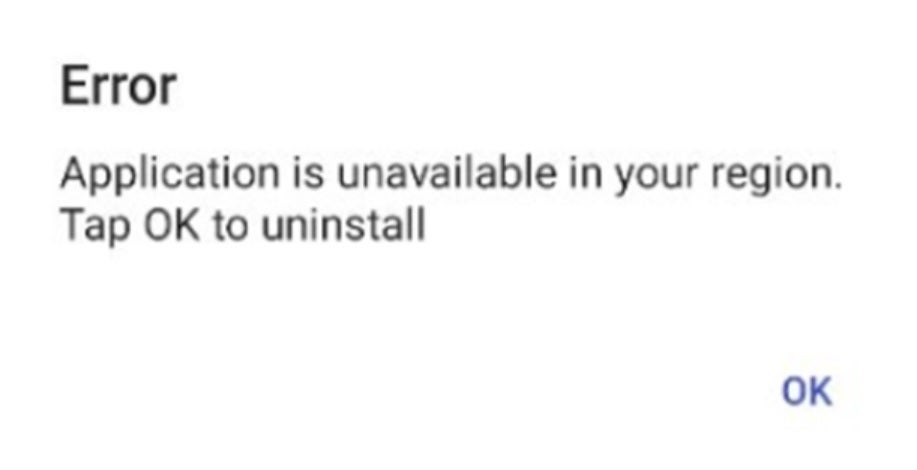
After installing the app you might see this notification while in reality, the app is setting itself up to run ads on your phone
Bitdefender writes, “Upon analysis, the campaign is designed to aggressively push adware to Android devices with the purpose of driving revenue. However, the threat actors involved can easily switch tactics to redirect users to other types of malware, such as banking Trojans to steal credentials and financial information or ransomware.” And while we want to warn you not to sideload apps from third-party app stores or websites, the truth is that some malware continues to live in the Google Play Store.
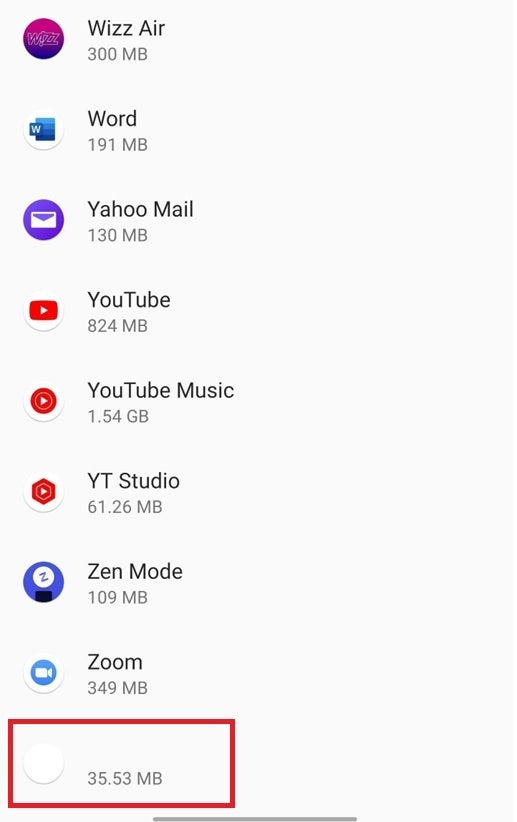
Without an icon, these apps show up in your installed apps list like the last entry found in this screenshot
Despite stories like this, your best bet is to stick to the Google Play Store and stay away from third-party app storefronts. And if you want to improve the odds of keeping your device malware-free, you might want to stick to installing apps from developers that you are familiar with even if that means limiting yourself to titles offered by big-name tech firms.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.

